When using a network connection, essential and complex communication protocols such as TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) take place mostly "behind-the-scenes" and are hidden beneath the user interface. This section shows the difference between Telnet's insecure, clear-text authentication, and the encrypted authentication used by OpenSSH, by capturing and analyzing some of the underlying data transfer.
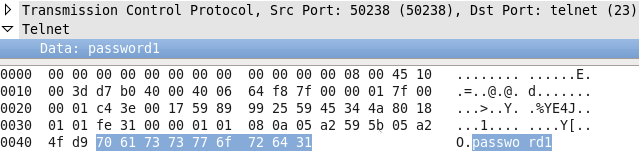
The following image shows a sample packet of connecting to a host via Telnet. Note that the password, password1, is clearly displayed in the data stream. This could easily expose the password to anybody analyzing the raw data on the network, leaving a host and its services vulnerable to attack:
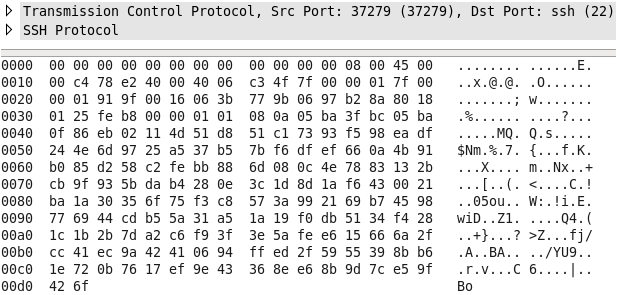
Compare the above image to the following image, which is a sample of connecting via OpenSSH. As OpenSSH uses encryption when providing credentials, the output is scrambled and is incomprehensible to anybody analyzing the raw packet data:
This feature alone is the main reason why utilities such as telnet and rlogin are considered insecure and out-dated. Providing encryption before credentials are sent, OpenSSH can allow for stronger security when communicating over any network, but most importantly over unknown, or untrusted ones.